This guide demonstrates how to setup automatic OpenSSH RSA public-key authentication for Windows (using OpenSSH v3.8.1p1-1) and Linux (using OpenSSH v5.3p1) PCs currently working with password authentication on a local network. The information for this guide was tested on PCs with WinXP and Lubuntu and may be applicable to other versions of Linux and Windows. You will need physical access to both PCs.
Public-key Cryptography
Public-key cryptography uses of a pair of matching keys, a public key and a private key, which are created at the same time using a key generation utility (ssh-keygen.exe is the key generation utility used in OpenSSH). A public key can be known to anyone and is used to encrypt data. The only way to decrypt data encrypted with the public key is with the matching private key. Although the two keys are related, a private key can’t be created from its matching public key. Public-key cryptography is widely used for public-key authentication to enable secure logins to servers without passwords and for digital or electronic signatures, and for certifying the authenticity of data signed by the private key.
The importance for using pubic key authentication can be summed up in this statement from the Ubuntu help pages: “If your SSH server is visible over the Internet, you should use public key authentication instead of passwords if at all possible. If you don’t think it’s important, try logging all of the malicious login attempts you get for the next week. My computer – a perfectly ordinary desktop PC – had over 4,000 attempts to guess my password and almost 2,500 break-in attempts in the last week alone.”
OpenSSH Public-key Authentication
OpenSSH can use either the RSA or DSA algorithms for public-key authentication. RSA stands for Rivest, Shamir and Adleman, the last names of the MIT team members who developed it. DSA stands for Digital Signature Algorithm, a US Government standard proposed by the National Institute of Standards and Technology. Although there are arguments for and against using one or the other, RSA is often the preferred choice because of its verification speed and key strength. See What is better for GPG keys – RSA or DSA? for a discussion on on this topic.
Steps for RSA Public-key Authentication
The following steps will setup RSA public-key authentication keys without a passphrase to enable automatic logins between Linux to Windows PCs on a local network. The instructions will be similar to setting up public-key authentication on remote hosts, except that SSH port 22 (if using the default port) must be forwarded to access remote servers from behind a router. When creating keys without a passphrase, as in this guide, make sure to place the public key on trusted hosts as it’s possible to compromise the remote computer should your private key fall into the wrong hands.
From the Windows PC
Step 1 – Generate Public Keys for the Windows PC
On the Windows PC, open a CMD window and type in the following command and hit ENTER to create a RSA key of 2048-bits (the default). The -t option specifies the type of key:
ssh-keygen -t rsa
Note: If you get a command is not recognized error, your path is incorrect. In this case, change to the bin folder where OpenSHH is installed to run the command.
When the command is executed, you will be prompted for a location to save the keys, and then for a passphrase as shown below. Hit ENTER to accept the default locations and to set NO passphrase.
Output:
Generating public/private rsa key pair Enter file in which to save the key (/home/username/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/username/.ssh/id_rsa Your public key has been saved in /home/username/.ssh/id_rsa.pub
The public key will be saved as .ssh/id_rsa.pub and your private key saved as .ssh/id_rsa in your home folder. The home directory was setup for the user(s) when OpenSSH was installed and configured.
Step 2 – Transfer Public Key to Linux PC
For the public key to be usable, it must be appended to the .ssh/authorized_keys file on the Linux computer and/or on other hosts you log into. If an authorized_keys file does not exist in your Linux computer’s home .ssh directory, create it. Also create a directory named “otherkeys“. The public key (ending in .pub) should be copied to “/home/username/.ssh/otherkeys” on the Linux computer using a USB drive, another medium, or remotely through Windows file sharing, SCP, or with SSH if it’s already working. Make sure to only copy the key and not move it.
After transferring the public key, at the Linux PC, open a terminal window or remotely connect to it and navigate to the .ssh folder in your home directory, and append the public key using the command below:
cat otherkeys/id_rsa.pub >> authorized_keys
Note: the key can also be cut and pasted into the authorized_keys file using a text editor
OR – remotely copying and appending the key with SCP and SSH
To remotely copy the public key to the Linux PC using SCP, enter the following in a command window. Note that there is no command for appending to a file using SCP. You will be asked for your password to use SCP remotely from the Windows PC:
scp ~/.ssh/id_rsa.pub [email protected]:/.ssh/otherkeys/
log in to the Linux PC with SSH, cd to the .ssh folder and execute the following command to append the key:
cat ~/.ssh/otherkeys/id_rsa.pub >> authorized_keys
Step 3 – Edit sshd_config
Open a command window and try to authenticate automatically to the Linux PC from the Windows PC using SSH. Make sure the SSH server was started on the Linux PC. It should work. If not, continue with the rest of this step and then recheck.
To troubleshoot the SSH public-key cryptography authentication processes, you can use the verbose option switch (-v) in the ssh command when logging in:
ssh -v [email protected]
If authentication didn’t work, goto the Linux PC and check that the permissions of the .ssh directory are set to octal 700. If not, use the following command from the Linux PC to change it:
# chmod 700 ~/.ssh/authorized_keys
If error messages were observed relating to the known_hosts file, find and delete the entries in the known_hosts file in the user .ssh directory of the Windows PC. The entries causing the errors will be numbered in the error message. After deleting the offending entry in the known_hosts file, test again to determine whether you can log onto the Linux PC without using a password.
After verifying you can log into the Linux PC without using a password, password authentication will still work should RSA not work for any reason, which is a security vulnerability. Password authentication can be turned off completely by changing the following entries in the etc/ssh/sshd_config file on the Linux PC. To use RSA authentication exclusively, make the following changes to the sshd_config to force public-key authentication and disable password authentication:
PasswordAuthentication no PubkeyAuthentication yes RSAAuthentication yes
After saving the file, restart the Linux PC SSH server using sudo /etc/init.d/ssh restart from a terminal on the Linux PC before logging in.
____________________________________________________________________________________
From the Linux PC
The steps are essentially the same as the previous steps with a few minor differences from the previous instructions
Step 1 – Generate Public Keys for the Linux Computer
From the Linux PC, open a terminal and type in the following command and hit ENTER to create a RSA key of 2048-bits (the default). The -t option specifies the type of key:
ssh-keygen -t rsa
When the command is executed, you will be prompted for a location to save the keys, and then for a passphrase as shown below. Hit ENTER to accept the default locations and to set NO passphrase.
Output:
Generating public/private rsa key pair Enter file in which to save the key (/home/username/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/username/.ssh/id_rsa Your public key has been saved in /home/username/.ssh/id_rsa.pub
The public key will be saved as .ssh/id_rsa.pub and your private key saved as .ssh/id_rsa in your home folder.
Step 2 – Transfer Public Key to Windows PC
For the public key to be usable, it must be appended to the .ssh/authorized_keys file on the Windows computer, other Linux PCs, and/or other hosts you log into. If the authorized_keys file does not exist in the user’s Windows .ssh directory, create it. Also create a directory named “otherkeys“. The public key (ending in .pub) should be copied to “\home\username\.ssh\otherkeys” on the Windows computer using a USB drive, another medium, or remotely with file sharing, SCP, or with SSH if it’s already working. Make sure to only copy the key and not move it.
After transferring the public key, at the Windows PC, navigate to the .ssh folder in your home directory, and append the public key to the authorized_keys file using the command below:
copy /b authorized_keys + otherkeys\id_rsa.pub authorized_keys
Note: the key can also be cut and pasted into the authorized_keys file using a text editor
OR – remotely copy the key using SCP and append it locally
To remotely copy the public key from the Linux PC to the Windows PC with SCP, enter the following in a terminal window. Note that there is no command for appending to a file using SCP. You will be asked for your password to use SCP remotely from the Linux PC. (Note that Windows doesn’t provide a way to easily append the public key remotely to the authorized_key file from the command-line)
scp ~/.ssh/id_rsa.pub [email protected]:.ssh/otherkeys/
This copies the public key to the otherkeys folder.
Physically log into the Windows PC and use an editor such as notepad or another app to append the key into the authorized_keys file.
OR – remotely copy the key using SCP to overwrite the authorized_keys file (caution: this overwrites the authorized_keys file. Use only if the authorized_keys file is empty or if it doesn’t matter if previous content is lost!)
execute the following to overwrite the authorized_keys file with your public key:
scp ~/.ssh/id_rsa.pub [email protected]:.ssh/authorized_keys
Step 3 – Edit sshd_config
In a terminal window try to log into the Windows PC with public-key authentication using SSH. Make sure the SSH server was started on the Windows PC. It should work. If not, continue with the rest of this step and then recheck.
To troubleshoot the SSH public-key cryptography authentication processes, you can use the verbose option switch (-v) in the ssh command as follows when logging in:
ssh -v [email protected]
If error messages errors were observed relating to the known_hosts file, find and delete those entries in the known_hosts file in the user .ssh directory in the Linux PC before continuing. The entries causing the errors will be numbered in the error message.
After deleting the offending entry in the known_hosts file, test again to determine whether you can log onto the Windows PC without using a password.
After verifying you can log into the Windows PC without using a password, password authentication will still work should RSA not work for any reason, which is also a security vulnerability. Password authentication can be turned off completely by changing the following entries in the OpenSSH\etc\sshd_config file on the Windows PC. To use RSA authentication exclusively, make the following changes to the sshd_config file to force public-key authentication and disable password authentication:
Note: If you still are unable to log in with pubic-key authentication at this point, do not make the following changes to the sshd_config file to force public-key authentication since you may need to login locally using your password with tools such as WinSCP. See below troubleshooting procedures:
StrictModes no PasswordAuthentication no PubkeyAuthentication yes RSAAuthentication yes
After saving the sshd_config file, restart the Windows PC SSH server first by stopping it using net stop opensshd and then restarting it using net start opensshd in a command window on the Windows PC to allow the config file to take effect before logging in.
If public-key authentication still doesn’t work, the most likely cause is that that the read/write/access permissions for the .ssh directory or for OpenSSH for the Windows PC are incorrect. See the below troubleshooting procedures below for further information.
Troubleshooting Windows OpenSSH server issues:
File permissions issues are a notorious problem for getting public-key authentication to work for OpenSSH on Windows. It’s probably the most confusing and most difficult issue to resolve. After much research and troubleshooting, I got it to work following this source from osdir.com. However, it’s uncertain whether it was one, all, or a combination of the suggestions that fixed the problem. In any case, below is a summary of the suggestions and how they were followed.
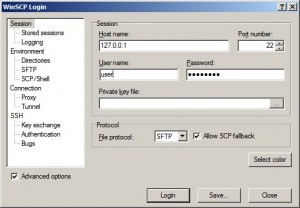
The tool used to change file permissions for the instructions below was WinSCP, with 127.0.0.1 as the host name and SFTP as the protocol (see screenshot below).
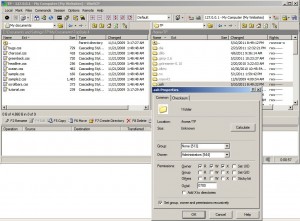
Permission changes were made using the properties window as shown in the screenshot below:
Here are the suggestions from osdir.com and how each was followed. Suggestions are preceded by an asterisk “*” and how the suggestions were followed are in bold :
*Change ownership of OpenSSH folder/subfolders to Administrators using Windows Explorer – Performed this for the folder and all subfolders using WinSCP.
*Grant Administrators full control of the OpenSSH folder – Same as above using Octal 0700
*From a command prompt, type “cacls c:\program files\openssh /t /e /c /g Administrators:F” * – Performed this for the c:\ssh folder, which was the OpenSSH folder on my PC.
Edit sshd_config file and set StrictModes to “no” – Changed the StrictModes entry to “no” and saved the file
*Under the user’s profile, grant Administrators (and only Administrators) full control of the .ssh folder and files – Did this for all folders and files for .ssh in the user directory (C:\Documents and Settings\user\.ssh).
*If this folder does not exist, it can be created by establishing an SSH connection to another box – Skipped. The .ssh file already existed
*On clients only, copy the private RSA key to the local .ssh folder and name it “id_rsa” – Skipped. The private keys already existed.
*Copy the client’s public RSA key to the desired server(s) by adding it to an “authorized_keys” text file located under the server’s .ssh folder – Skipped. Done previously.
* To use publickey authentication, use the SSH command line switch “-o PreferredAuthentications=publickey”. Alternately, you can modify the ssh_config file to make this the default – Skipped.
If the above instructions worked:
Decide whether to use RSA authentication exclusively. If so, edit the sshd_config file per the instructions above.
Note: many instructions on various web sites suggest copying public keys to the user’s .ssh directory on the server. If you do, make sure to place them in a separate folder such as a otherkeys folder or another name such as username_key since existing public keys (id_rsa.pub) will be overwritten if multiple PCs are used to access the same machine.




Spelling error report
The following text will be sent to our editors: